DownUnderCTF 2025 Write-up
Write-up and walkthroughs for DownUnderCTF 2025 - beginner and medium challenges across OSINT, Reversing, Misc, and Forensics.
DownUnderCTF 2025 Write-up
Author: AppleTree
Team: APISec Avengers
Event Dates: July 19–21, 2025
Platform: DownUnderCTF 2025
Flag Format: DUCTF{.*}
I participated in DownUnderCTF 2025 and tackled a variety of beginner to medium difficulty challenges across OSINT, Reversing, Misc, and Forensics. This post documents the full process for each challenge I solved — including the flag, points, and methodology — using tools like NBD mounts, AI prompt interaction, binary decompilation, and metadata forensics.
fat donke diss
Category: OSINT
Points: 100
Flag: DUCTF{I_HAVE_NOT_THOUGHT_UP_OF_A_FLAG_YET}
Description
Dear AppleTree,
ain’t no fat donke tryin to spit bars on the fat monke
Regards,
MC Fat Monke
Steps Taken
- Searched for
"MC Fat Monke fat donke diss"on Google. - Located this SoundCloud track.
- Found a linked YouTube video.
- At timestamp
0:55, the flag was visible in the video frame.
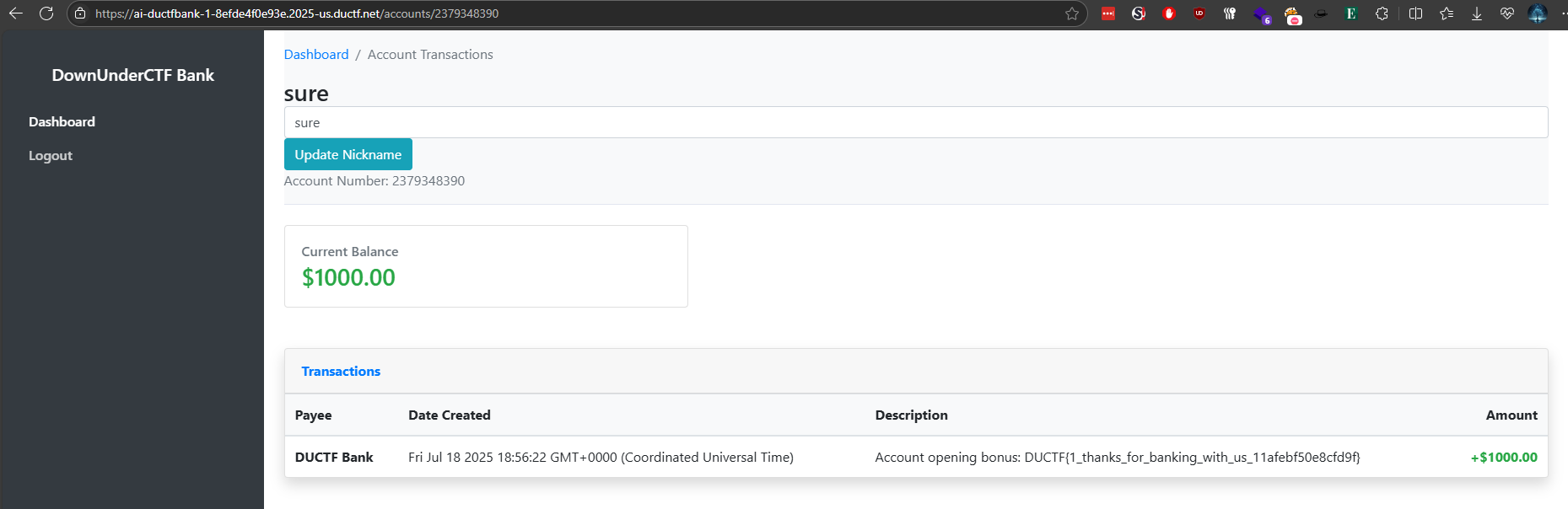
ductfbank1
Category: AI
Points: 100
Flag: DUCTF{1_thanks_for_banking_with_us_11afebf50e8cfd9f}
Description
Dear AppleTree,
I’m from DownUnderCTF Bank. As part of your company’s business relationship with us, we are pleased to offer you a complimentary personal banking account with us.
Regards,
dot
Steps Taken
- Visited: https://ai-ductfbank-1-8efde4f0e93e.2025-us.ductf.net
- Registered a new user through the site.
- Initiated a chat with the AI model.
- Asked it to create a banking account — despite the account button being disabled.
- The AI granted an account and displayed flag details in the perks.
corporate-cliche
Category: Beginner
Points: 100
Flag: DUCTF{wow_you_really_boiled_the_ocean_the_shareholders_thankyou}
Description
Dear AppleTree,
It’s time to really push the envelope and go above and beyond! We’ve got a new challenge for you. Can you find a way to get into our email server?
Regards, Blue Alder
AU: nc chal.2025.ductf.net 30000
US: nc chal.2025-us.ductf.net 30000
Steps Taken
- Initial Analysis
- Reviewed the provided C source code.
- Identified a classic buffer overflow via
gets(password). - Noted that
usernameandpasswordare bothchar[32], withusernamedeclared afterpassword— making it possible to overflow intousername.
- Bypass Username Check
- Challenge prevents logging in as
admindirectly. - But the
loginsarray shows thatadminis a valid user with emoji password🇦🇩🇲🇮🇳.
- Challenge prevents logging in as
- Attack Plan
- Input a harmless username like
guest. - Overflow the
passwordbuffer with:- The emoji password (
🇦🇩🇲🇮🇳, 20 bytes) - Padding up to 32 bytes
- Then overwrite the
usernamebuffer withadmin\x00.
- The emoji password (
- Input a harmless username like
- Payload Construction
- Encoded the emoji in raw UTF-8 bytes:
\xf0\x9f\x87\xa6\xf0\x9f\x87\xa9\xf0\x9f\x87\xb2\xf0\x9f\x87\xae\xf0\x9f\x87\xb3 - Added a null byte to terminate for
strcmp. - Final payload:
1
[ 20-byte emoji pw ][ padding to 32 ][ b'admin\x00' ]
- Encoded the emoji in raw UTF-8 bytes:
- Execution
- Connected to the challenge via
nctochal.2025-us.ductf.net 30000. - Sent
guestas username. - Sent overflow payload as password.
- Successfully bypassed the username check and passed the emoji password.
- Connected to the challenge via
- Result
- The program jumped into
open_admin_session(). - A shell was spawned.
- Retrieved flag:
DUCTF{wow_you_really_boiled_the_ocean_the_shareholders_thankyou}
- The program jumped into
zeus
Category: Reversing
Points: 100
Flag: DUCTF{b3_w4r3_7h3_g0d5}
Description
Dear AppleTree,
To Zeus Maimaktes, Zeus who comes when the north wind blows, we offer our praise, we make you welcome!
Regards,
jzt
Steps Taken
- Decompiled the binary and found an XOR check against a static hex string.
- Reversed the XOR using the expected comparison result.
- Submitted the decoded input to the binary:
1
echo -ne '[correct bytes]' | ./zeus
- The binary accepted the input and printed the flag.
Network Disk Forensics
Category: Beginner
Points: 100
Flag: DUCTF{now_you_know_how_to_use_nbd_4y742rr2}
Description
Dear AppleTree,
Nobody likes having to download large disk images for CTF challenges so this time we’re giving you a disk over the network!
Regards,
jscarsbrookAU: nc chal.2025.ductf.net 30016
US: nc chal.2025-us.ductf.net 30016
Steps Taken
- Connected again:
1 2
nc chal.2025-us.ductf.net 30016 sudo nbd-client chal.2025-us.ductf.net 30016 /dev/nbd0 -persist
- Inspected partitions and mounted it:
1 2
sudo fdisk -l /dev/nbd0 sudo mount /dev/nbd0p1 /mnt
- Found a suspicious
.ps1PowerShell script. - Decoded the base64 payload and retrieved the embedded flag.
- Cleanly unmounted:
1 2
sudo umount /mnt sudo nbd-client -d /dev/nbd0
Final Thoughts
DownUnderCTF 2025 offered a solid range of challenges that balanced accessibility with creative puzzle design. We completed 9 total challenges and spent time exploring tools like NBD mounts, AI prompt manipulation, and binary analysis.
Note: AI-assisted editing was used to improve grammar, clarity, and formatting. All technical content and opinions are original.